This post will show:
- Where Global Settings For Windows Hello For Business Can Be Set
- Why Its Current Setup is a Big Problem For Less-Centralized Organizations
- The Workaround For This Issue
How Delegated Admins Tend To Work
If you run Intune, and you want to empower your departments to offer their own support, there’s a way to do this:
Use scope tags to tag certain things in Intune, assign that scope tag to a role, assign the role to a group, and put your delegated admins in that group.
In this way, the role limits what functions these delegated admins can perform, and the scope limits them to using this access on their own department’s devices.
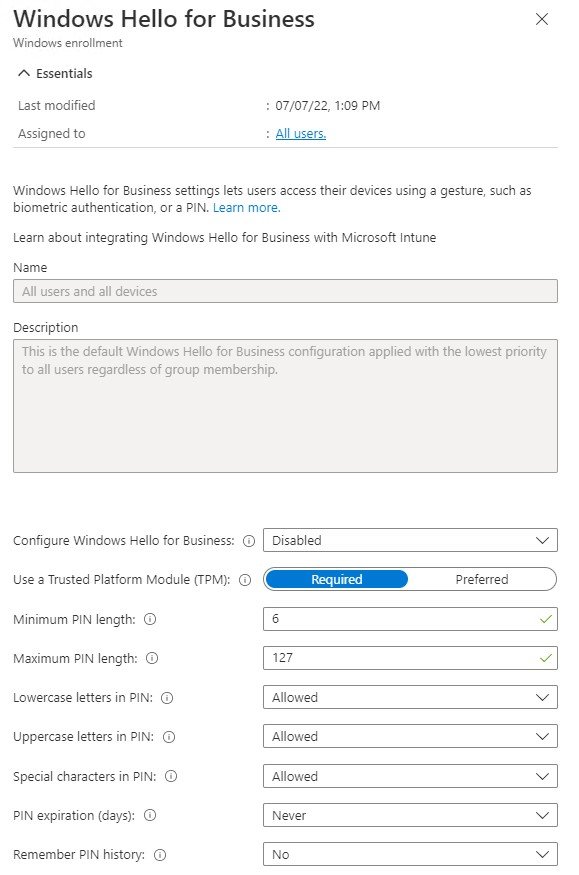
However, if any of these admins can access the “Enroll Devices” screen in the Intune UI, they can turn on and edit the GLOBAL Windows Hello For Business Settings.
This doesn’t seem to make sense.
Recently Microsoft added the ability to put WHFB settings into a Configuration Profile.
These can be scoped, which is ideal for delegated admins to use to turn on WHFB for their own departments.
However, so long as they have access to the Windows Enrollment screen, they can change the GLOBAL settings too.
Access To Every Option On This Screen Can Be Limited, Except…
On this Windows Enrollment Screen, the Automatic Enrollment option can be limited through Intune roles.
Access to the ESP, Co-Management Settings, Deployment Profiles, Autopilot Devices, and the Intune Connector — can all be limited.
Access to Windows Hello For Business cannot. It’s not included in any Intune role permissions.
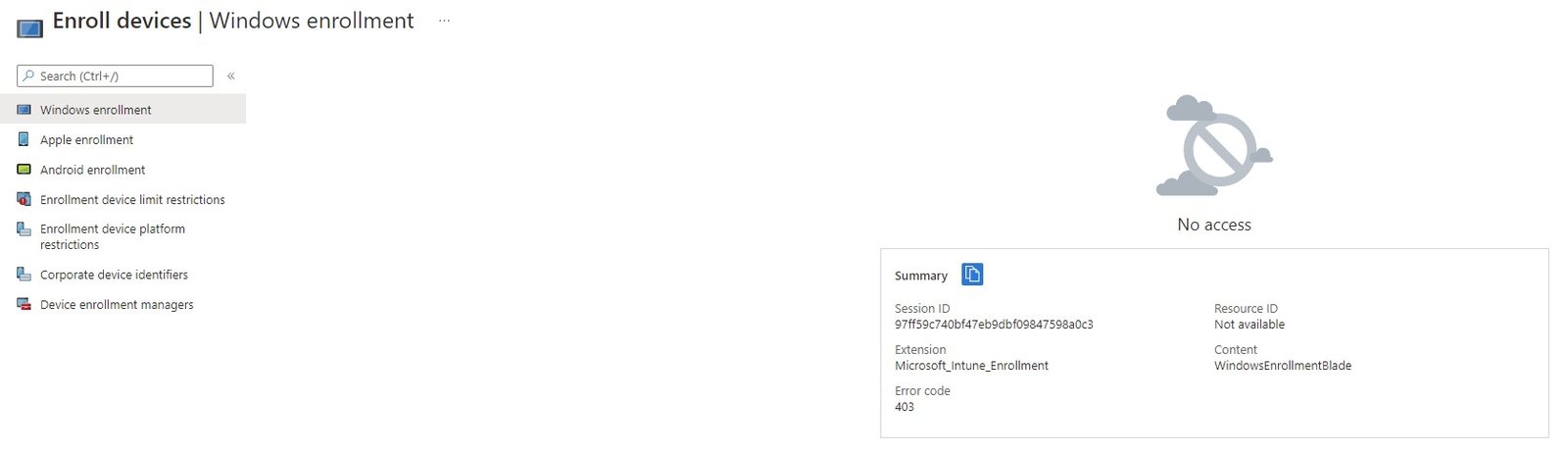
Anyone who can see the button here, can change it.
So any delegated admin who can see this page can, as of September 2022, turn on/off or change global Windows Hello For Business settings.
Why? I have no idea.
It’s almost as if this option is going away soon (now that WHFB can be turned on using configuration profiles, and a profile can target all devices if needed), and they just threw the option here until it gets eliminated.
Workaround: Block Access To The Windows Enrollment Screen.
Direct URLs Still Work.
Until Microsoft changes the way this works, the workaround here is to block access to this page entirely in your custom Intune roles.
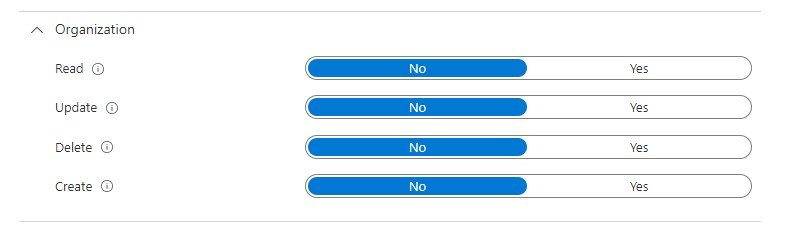
It’s not immediately clear what does this, but testing found that removing the Organization permissions can block someone from seeing the Windows Enrollment screen.
Interestingly, this doesn’t block access to the direct URLs for Autopilot info, or other Windows Enrollment screens.
Delegated Admins can use the direct URL for the Autopilot Devices blade, for example.
They’ll just be unable to navigate to it using the Intune UI.
And again, if these lower-level admins need to enable Windows Hello For Business, they can now create a Configuration Profile, scoped to their department’s devices, that can do it.
It’s still baffling why this option hasn’t been removed from Windows Enrollment, or at least why it’s not included in any of the Intune Custom Role permissions that I’ve been able to find.
Recreate this issue on your own with a M365 Developer Account
I do all my testing, scenario screenshots etc on my own private Intune tenant.
A free Microsoft 365 Developer Program account doesn’t come with Azure credits, but it does give free access to Azure AD and Intune.
With a few virtual machines on my desktop, I have just enough test “devices” to run some experiments.
Setup some custom Intune roles, a few delegated admin users and groups, a few Intune scopes, and you’re pretty much good to go.