[et_pb_section fb_built=”1″ _builder_version=”3.22″ global_colors_info=”{}”][et_pb_row column_structure=”1_4,3_4″ disabled_on=”off|off|off” _builder_version=”3.25″ custom_margin=”||11px|||” custom_padding=”10px|10px|10px|10px|true|true” global_colors_info=”{}”][et_pb_column type=”1_4″ _builder_version=”3.25″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_team_member name=”Craig Wall” image_url=”https://craigtwall.com/wp-content/uploads/2019/01/Craig-Transparent-150×150.png” _builder_version=”4.14.7″ _module_preset=”default” text_orientation=”center” global_module=”212111″ saved_tabs=”all” global_colors_info=”{}”]
Public sector systems admin, specializing in device management, mobility and deployment.
[/et_pb_team_member][et_pb_blurb title=”Facebook” url=”https://www.facebook.com/craig.wall.7″ url_new_window=”on” use_icon=”on” font_icon=”||divi||400″ icon_placement=”left” admin_label=”Facebook” _builder_version=”4.14.7″ _module_preset=”default” text_orientation=”center” custom_margin=”||2px||false|false” custom_padding=”||||false|false” link_option_url=”https://www.facebook.com/craig.wall.7″ link_option_url_new_window=”on” global_module=”212112″ saved_tabs=”all” global_colors_info=”{}”][/et_pb_blurb][et_pb_blurb title=”LinkedIn” url=”https://www.linkedin.com/in/craigtwall/” url_new_window=”on” use_icon=”on” font_icon=”||divi||400″ icon_placement=”left” admin_label=”Linkedin” _builder_version=”4.14.7″ _module_preset=”default” text_orientation=”center” custom_margin=”||2px||false|false” custom_padding=”||||false|false” link_option_url=”https://www.linkedin.com/in/craigtwall/” link_option_url_new_window=”on” global_module=”212113″ saved_tabs=”all” global_colors_info=”{}”][/et_pb_blurb][et_pb_blurb title=”Twitter” url=”https://twitter.com/craigtwall” url_new_window=”on” use_icon=”on” font_icon=”||divi||400″ icon_placement=”left” admin_label=”Twitter” _builder_version=”4.14.7″ _module_preset=”default” text_orientation=”center” custom_margin=”||2px||false|false” custom_padding=”||||false|false” link_option_url=”https://twitter.com/craigtwall” link_option_url_new_window=”on” global_module=”212114″ saved_tabs=”all” global_colors_info=”{}”][/et_pb_blurb][et_pb_blurb title=”GitHub” image=”data:image/svg+xml;base64,PHN2ZyB3aWR0aD0iMTA4MCIgaGVpZ2h0PSI1NDAiIHZpZXdCb3g9IjAgMCAxMDgwIDU0MCIgeG1sbnM9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvc3ZnIj4KICAgIDxnIGZpbGw9Im5vbmUiIGZpbGwtcnVsZT0iZXZlbm9kZCI+CiAgICAgICAgPHBhdGggZmlsbD0iI0VCRUJFQiIgZD0iTTAgMGgxMDgwdjU0MEgweiIvPgogICAgICAgIDxwYXRoIGQ9Ik00NDUuNjQ5IDU0MGgtOTguOTk1TDE0NC42NDkgMzM3Ljk5NSAwIDQ4Mi42NDR2LTk4Ljk5NWwxMTYuMzY1LTExNi4zNjVjMTUuNjItMTUuNjIgNDAuOTQ3LTE1LjYyIDU2LjU2OCAwTDQ0NS42NSA1NDB6IiBmaWxsLW9wYWNpdHk9Ii4xIiBmaWxsPSIjMDAwIiBmaWxsLXJ1bGU9Im5vbnplcm8iLz4KICAgICAgICA8Y2lyY2xlIGZpbGwtb3BhY2l0eT0iLjA1IiBmaWxsPSIjMDAwIiBjeD0iMzMxIiBjeT0iMTQ4IiByPSI3MCIvPgogICAgICAgIDxwYXRoIGQ9Ik0xMDgwIDM3OXYxMTMuMTM3TDcyOC4xNjIgMTQwLjMgMzI4LjQ2MiA1NDBIMjE1LjMyNEw2OTkuODc4IDU1LjQ0NmMxNS42Mi0xNS42MiA0MC45NDgtMTUuNjIgNTYuNTY4IDBMMTA4MCAzNzl6IiBmaWxsLW9wYWNpdHk9Ii4yIiBmaWxsPSIjMDAwIiBmaWxsLXJ1bGU9Im5vbnplcm8iLz4KICAgIDwvZz4KPC9zdmc+Cg==” icon_placement=”left” admin_label=”Github” _builder_version=”4.14.7″ _module_preset=”default” text_orientation=”center” custom_margin=”||2px||false|false” custom_padding=”||||false|false” global_module=”212117″ saved_tabs=”all” global_colors_info=”{}”][/et_pb_blurb][et_pb_divider color=”#111111″ admin_label=”Divider” _builder_version=”3.2″ global_module=”212118″ saved_tabs=”all” global_colors_info=”{}”][/et_pb_divider][et_pb_cta title=”My Endpoint Manager List on Twitter” button_url=”https://twitter.com/i/lists/1376584964146364437″ url_new_window=”on” button_text=”100+ Members” admin_label=”Twitter List Box” _builder_version=”4.14.7″ _module_preset=”default” background_color=”#161e8c” button_alignment=”center” link_option_url=”https://twitter.com/i/lists/1376584964146364437″ link_option_url_new_window=”on” hover_enabled=”0″ global_module=”212119″ saved_tabs=”all” global_colors_info=”{}” sticky_enabled=”0″][/et_pb_cta][/et_pb_column][et_pb_column type=”3_4″ _builder_version=”3.25″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_post_title _builder_version=”4.14.7″ _module_preset=”default” title_font=”Poppins|700|||||||” title_text_color=”#000000″ title_font_size=”28px” custom_padding=”10px|10px|10px|10px|true|true” global_colors_info=”{}”][/et_pb_post_title][et_pb_text admin_label=”Introduction” _builder_version=”4.14.7″ _module_preset=”default” text_font=”Poppins||||||||” text_text_color=”#333333″ text_font_size=”20px” text_line_height=”1.5em” custom_margin=”||11px|||” custom_padding=”10px|10px|10px|10px|true|true” global_colors_info=”{}”]
I recently setup an SCCM Co-Management home lab.
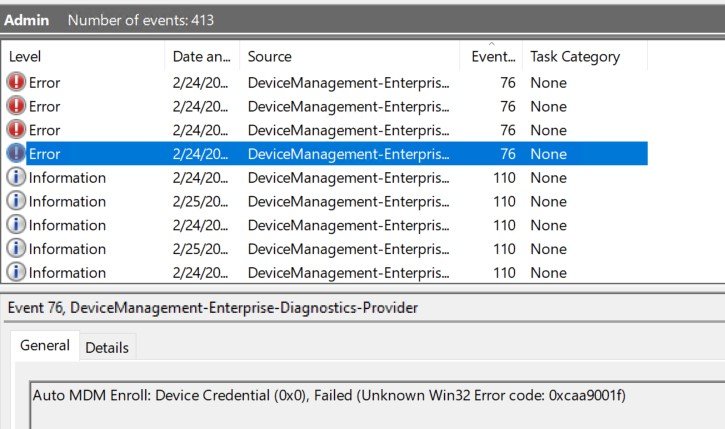
When testing the MDM enrollment to Intune of an AD-joined device, I ran into a 0xcaa90014 error. The failure showed up in two places:
In Windows Event Viewer, it shows up in DeviceManagement-Enterprise-Diagnostics-Provider as:
Event ID 76: Auto MDM Enroll: Device Credential (0x0), Failed (Unknown Win32 Error code: 0xcaa9001f)
A separate error shows up in the client’s Co-Management logs, found under %WINDIR%\CCM\Logs\CoManagementHandler.log:
[/et_pb_text][et_pb_text admin_label=”Main Post Body” _builder_version=”4.14.7″ _module_preset=”default” text_font=”Poppins||||||||” text_text_color=”#333333″ text_font_size=”20px” text_line_height=”1.5em” custom_margin=”||11px|||” custom_padding=”10px|10px|10px|10px|true|true” global_colors_info=”{}”]
The reason for the 0xCAA9001F error is that the device is not logged in with a credential that Azure AD recognizes.
My home lab was using an unverified domain — my home lab was using a domain like test.contoso.com, but since it’s unverified, the user accounts were synced to Azure AD as walldev.onmicrosoft.com.
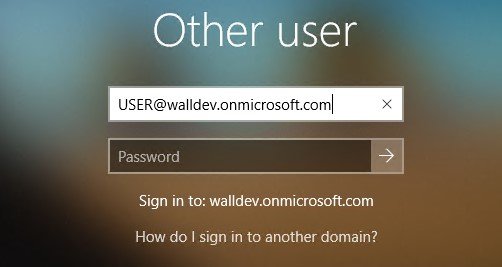
I was logged into my test client VM as CONTOSO\USER when I had to sign in as an AAD user — as a @walldev.onmicrosoft.com user.
[/et_pb_text][et_pb_text admin_label=”Main Post Body” _builder_version=”4.14.7″ _module_preset=”default” text_font=”Poppins||||||||” text_text_color=”#333333″ text_font_size=”20px” text_line_height=”1.5em” header_2_font=”|||on|||||” custom_margin=”||11px|||” custom_padding=”10px|10px|10px|10px|true|true” global_colors_info=”{}”]
Solution: Create an Alternative UPN Suffix in Active Directory Domains and Trusts
On your AD domain, load Active Directory Domains and Trusts.
Right-click the “Active Directory Domains and Trusts” heading and click Properties.
Under “Alternative UPN Suffix”, add in the domain that your Azure AD tenant is using. In my case this was walldev.onmicrosoft.com:
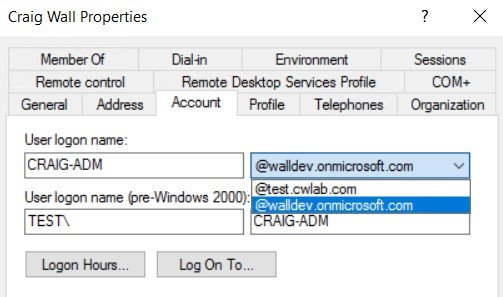
Then we need to configure your user account to use this alternate UPN suffix.
On your AD domain, start AD Users and Computers
Search for the user account you’re using to login to your AD client for MDM enrollment. Right-click it and go to Properties.
Go to the Account tab.
Under User Logon name, there’s a pulldown box next to your username that shows the local domain.
Click the pulldown and select the alternate UPN suffix that now shows up there.
Click Apply and then exit.
Once I did this, I was able to login to my VM domain client as USER@walldev.onmicrosoft.com instead of CONTOSO\USER.
And almost immediately after that login completed, the MDM enrollment succeeded.
If this doesn’t do the trick for you, then see the linked MS Docs article at the bottom of this post, which runs through another possible solution (enabling both AD User Discovery and Azure AD User Discovery)
[/et_pb_text][et_pb_text disabled_on=”off|off|off” admin_label=”Main Post Body” _builder_version=”4.14.7″ _module_preset=”default” text_font=”Poppins||||||||” text_text_color=”#FFFFFF” text_font_size=”20px” text_line_height=”1.5em” header_text_color=”#FFFFFF” header_2_font=”Poppins|||on|||||” header_2_text_color=”#FFFFFF” header_2_letter_spacing=”1px” use_background_color_gradient=”on” background_color_gradient_start=”#041216″ background_color_gradient_end=”#211f9b” background_color_gradient_direction=”16deg” custom_padding=”10px|10px|10px|10px|false|false” border_radii=”on|15px|15px|15px|15px” global_colors_info=”{}”]
The M365 Developer Program Makes This Setup Free, By the Way
Intune licenses normally require an E3/A3 or E5/A5 license.
However, sign up for the M365 Developer Program, which is free, and you get Azure AD plus 25 licenses at the A5/E5 level to test with!
The only drawback: It doesn’t come with any Azure credits.
So if you want to implement the next logical step for testing — a Cloud Management Gateway — the resources it sets up will cost money.
[/et_pb_text][et_pb_text admin_label=”Main Post Body” _builder_version=”4.14.7″ _module_preset=”default” text_font=”Poppins||||||||” text_text_color=”#333333″ text_font_size=”20px” header_2_font=”|||on|||||” header_3_letter_spacing=”1px” custom_margin=”||11px|||” custom_padding=”10px|10px|10px|10px|true|true” global_colors_info=”{}”]
References:
Microsoft: MDM enrollment fails with error 0xcaa9001f for co-managed Windows devices
TechDirectArchive: Fix NSLOOKUP Error: Can’t Find Non-Existent Domain
[/et_pb_text][et_pb_text disabled_on=”on|on|on” admin_label=”PowerShell Code Block” _builder_version=”4.14.7″ _module_preset=”default” text_font=”Poppins||||||||” text_font_size=”22px” disabled=”on” global_colors_info=”{}”]
New-CMBoundaryGroup -Name 'Default Boundary Group' ` -Description 'All Boundaries in the ConfigMgr environment' ` -DefaultSiteCode $CMSiteCode `
[/et_pb_text][et_pb_divider _builder_version=”4.14.7″ _module_preset=”default” width=”65%” module_alignment=”center” global_colors_info=”{}”][/et_pb_divider][/et_pb_column][/et_pb_row][et_pb_row _builder_version=”3.25″ background_size=”initial” background_position=”top_left” background_repeat=”repeat” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”3.25″ custom_padding=”|||” global_colors_info=”{}” custom_padding__hover=”|||”][et_pb_divider color=”#111111″ _builder_version=”3.2″ global_colors_info=”{}”][/et_pb_divider][et_pb_text _builder_version=”4.14.7″ header_3_font=”Poppins|500|||||||” header_3_text_align=”center” header_3_letter_spacing=”1px” global_colors_info=”{}”]
Check Out More
[/et_pb_text][et_pb_blog fullwidth=”off” posts_number=”3″ include_categories=”all” show_thumbnail=”off” use_manual_excerpt=”off” excerpt_length=”0″ show_author=”off” show_excerpt=”off” _builder_version=”4.14.7″ _module_preset=”default” header_font=”Poppins|700|||||||” header_font_size=”14px” global_colors_info=”{}”][/et_pb_blog][/et_pb_column][/et_pb_row][/et_pb_section]